Once behind the captive portal, the page initiates the Windows Test Connectivity Status Indicator, a legitimate service that determines whether a device has Internet access by sending an HTTP GET request to hxxp://www.msftconnecttest[.]com/redirect. That site, in turn, redirects the browser to msn[.]com. As Thursday’s post explained:
Once the system opens the browser window to this address, the system is redirected to a separate actor-controlled domain that likely displays a certificate validation error which prompts the target to download and execute ApolloShadow. Following execution, ApolloShadow checks for the privilege level of the ProcessToken and if the device is not running on default administrative settings, then the malware displays the user access control (UAC) pop-up window to prompt the user to install certificates with the file name CertificateDB.exe, which masquerades as a Kaspersky installer to install root certificates and allow the actor to gain elevated privileges in the system.
The following diagram illustrates the infection chain:
ApolloShadow invokes the GetTokenInformationType API to check if it has sufficient system rights to install the root certificate. If not, the malware uses a sophisticated process that spoofs a page at hxxp://timestamp.digicert[.]com/registered, which in turn sends the system a second-stage payload in the form of a VBScript.
Once decoded, ApolloShadow relaunches itself and presents the user with a User Access Control window seeking to elevate its system access. (Microsoft provided many more technical details about the technique in Thursday’s post.)
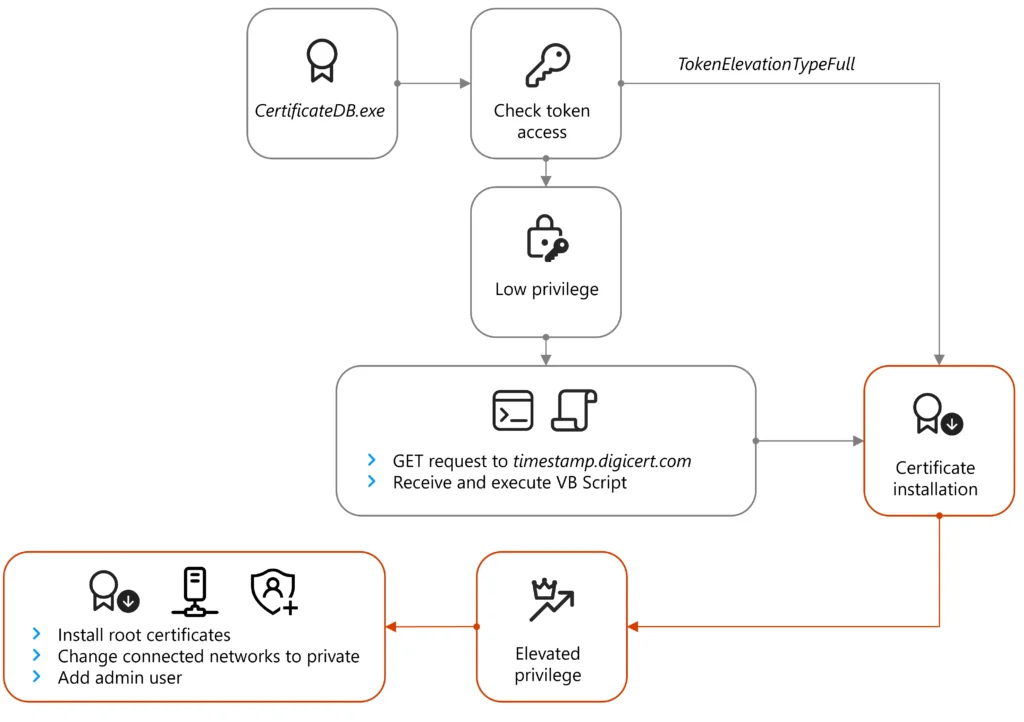
If ApolloShadow already has sufficient system rights, the malware configures all networks the host connects to as private.
“This induces several changes including allowing the host device to become discoverable and relaxing firewall rules to enable file sharing,” Microsoft explained. “While we did not see any direct attempts for lateral movement, the main reason for these modifications is likely to reduce the difficulty of lateral movement on the network.” (The Microsoft post also provided technical details about this technique.)
Microsoft said the ability to cause infected devices to trust malicious sites allows the threat actor to maintain persistence, likely for use in intelligence collection.
The company is advising all customers operating in Moscow, particularly sensitive organizations, to tunnel their traffic through encrypted tunnels that connect to a trusted ISP.

